|
Getting your Trinity Audio player ready...
|
Between December 27th – 28th last year, one of Norway’s largest media groups – Amedia – was hit by a catastrophic ransomware attack that shut down its printing presses and also impacted the company’s advertising and subscription systems. Here are the key takeaways… Editor’s Note: Our thanks to Jim Bilton of wessendenbriefing for the original story, insights, and key takeaways.
Amedia is the largest publisher of local media in Norway, with a thousand editorial staff covering news across 89 local newspapers, 3 trade journals, and two national news brands (Nettavisen and Nationen).
Last Christmas it suffered a major cyberattack on its central computer systems which took out 500 internal servers and brought most of the company’s operations to a halt. Print newspaper editions were shut down, whilst Amedia’s advertising and subscription platforms were similarly hit with readers unable to either subscribe or unsubscribe.
On the night of Tuesday 28 December, several of Amedia’s central computer systems were shut down. The production of online newspapers is going as normal, but no paper newspapers will be published on Wednesday. This is because systems for publishing paper newspapers, advertisements and subscription management do not work as normal.
Amedia statement, translated
By any measure, the attack was catastrophic not least because the company’s subscription systems contained user data, names and addresses, phone numbers, subscription forms, and history. Fortunately, credit card details and passwords were not affected according to the company, yet the damage had been done.
The fallout for Amedia was severe. Whilst the police investigated the crime (paying ransoms for cyberattacks is illegal in Norway), the company worked day and night over several weeks to clean its servers and restore 3,000 user terminals. In all, it took €3 million and nine months to get back to where it was before the attack, not to mention the loss of ongoing tech development and, crucially, user trust.
Key Lessons for Publishers
As a case study in cybercrime, the viewpoint of security professionals varies from critical (“yet another organization that’s in distress due to under-investment in IT security”) to downright scathing.
Writing in the wessendenbriefing, Jim Bilton says that media companies are easy targets as media isn’t as clued-up as other industries, “The scary fact is that attacks on media companies are increasing, by both individual, commercial hackers and nation-states. Part of the reason is that media is not as tech-savvy as other industries.”
Another scary fact is that Ransomware-as-a-Service is now available on the Dark Web. Pay your subscription and (you can) go off and attack a company’s computer system.
Jim Bilton, wessendenbriefing
Here are Bilton’s key takeaways from Amedia’s hack:
- Keep a print or offline version of your key recovery documents
Amedia’s disaster recovery manuals were held electronically on one of the infected servers.
- Keep back-up data safely stored offsite
To Amedia’s credit, the company stored its backup data offsite. Lineup Systems, the news media tech specialist, helped Amedia restore its system to full functionality using its SaaS system.
- Upgrade your detection software
Whilst a crucial point, Bilton writes that “the attack was as much about human processes as the tech – it was the sloppy distribution of passwords by a handful of users that allowed the virus in.”
- Consider moving into cloud-based systems rather than company-based, in-house servers.
Whilst SaaS systems are no guarantee of cyberattack prevention (and can lull users into a false sense of security), there are a number of highly secure, trusted suppliers that cater to the media industry. Bilton cites Lineup’s “immutable storage” service as an example.
The Importance of Transparency
Cybersecurity specialist, Charlie Maclean-Bristol, adds that Amedia should be applauded for the transparency of its communication with users, “Amedia was very upfront about the hack. There was no doubt they had a cyberattack. There is also a separate tab on the website about the data hack, both of which are good practices.”
Breaking down a timeline of events, Maclean-Bristol writes that the media company immediately humanized its communications by featuring a very prominent picture (and statement) from Pål Nedregotten, who was Executive Vice President in charge of Product, Editorial and Subscriptions at Amedia.
I personally think it’s an excellent idea to incorporate communications in the information pack. Especially when it is a computer or IT story to humanise it and behind every computer system, there is a real person.
Charlie Maclean-Bristol, Training Director, FBCI, FEPS
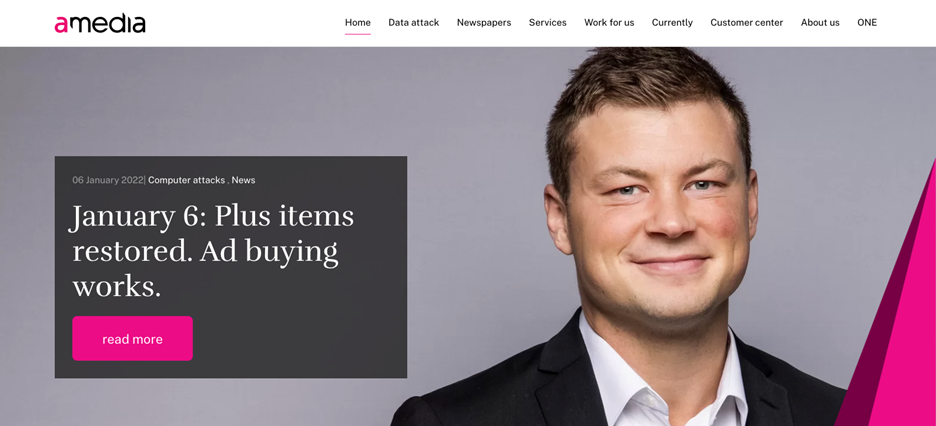
Maclean-Bristol’s chief criticism was the unavailability of a contact helpline, “As far as I can see, there was no helpline or contact details of a member of staff in case you wanted to contact the organization for more information to confirm whether you had been affected. Good practice suggests there should be a means for people to get information straight from the organization and not have to wait until they are informed.”
Overall, however, Maclean-Bristol was impressed with the company’s response, “I believe that Amedia has done an excellent job at providing information to their customers and staff. They have been open about the incident and its impact, provided regular updates on the status of services and when they are likely to be back.
“There are a number of actions that Amedia could improve upon, but on the whole, I think their response has been fairly good. When you provide B2C services and have a large public customer base, you cannot hide a cyber incident.”
To receive a sample issue of the wessendenbriefing please email info@wessenden.com